Hashing vs Encryption – Hashing refers to permanent data conversion into message digest while encryption works in two ways, which can encode and decode the data.
Hashing helps protect the integrity of the information and Encryption is used to secure the data from the reach of third parties. They both look indistinguishable but are dissimilar from each other. Hashing emphasizes the integrity of the information while Encryption focuses on the confidentiality of the data. Let us review both hashing and encryption to get a clear idea about their functionality and differences.
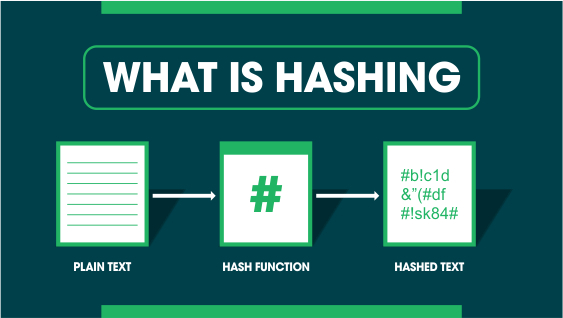
What is Hashing?
Hashing is the process of changing a plain text or a key to a hashed value by applying a hash function. Usually, the input length is greater in size than the output hash value.
Hashing is a one-way encryption process such that a hash value cannot be reverse-engineered to get to the original plain text.
Hashing is used in encryption to secure the information shared between two parties. The passwords are transformed into hash values so that even if a security breach occurs, PINs stay protected. We have already shared information about Hashing Parameters which you can read.
How Does Hashing Work?
Two different keys can produce identical hash values which result in a collision. For hashing to work efficiently, you should modify the hashing algorithm so that there are minimum chances of collision. The hashing algorithms then produce different hash values for alternate keys. Some key characteristics of hashing include:
- One input string should have one specific hash value
- Hashing should be irreversible
- A hash function must be quick
- A slight change in the input should produce a different hash
Some Common Hashing Algorithms
The following are the most used hashing functions:
1) Message Digest (MD5)
After finding severe security issues in MD4 – MD5 came as an advanced form of MD4. MD5 generates 128-bit outputs for a variable length of inputs. As a successor to MD4, it covered a lot of security threats but failed to provide full data security services. Though widely used, the main issues being raised with the use of MD5 are its vulnerability and collisions.
2) SHA
SHA means Secure Hashing Algorithm; it was developed for the first time by the National Security Agency. This algorithm got updates repeatedly to improve security flaws in the old genre. Now, SHA-2 is being used by many firms for cryptographic purposes.
3) Tiger Algorithm
The Tiger cypher algorithm is a faster and more efficient algorithm in comparison to the MD5 and SHA families. It has a 192-bit hashing system and is mostly used in computers of the new era. Tiger2 is an advanced form of this algorithm that is even more powerful than the Tiger algorithm.
4) Message Digest Algorithm (MD4)
Message Digest Algorithm (MD4) is a cryptographic hash function carrying a 128-bit digest. MD4 had a security flaw due to the first collision attack found in 1995. After that, a few newer attacks also affected this hash function. Ronald Rivest generated MD4 in 1990 and has influenced the designs of MD5, SHA-1, and RIPEMD algorithms.
5) RIPMEND
Hans Dobbertin has designed the RIPMEND cryptographic hashing algorithm, which has a length of the 164-bit digest. It is created using the EU project RIPE framework.
6) WHIRLPOOL Algorithm
Vincent Rijmen and Paul Barreto have designed the WHIRLPOOL algorithm, which considers any message of a length less than 2256 bits and in return offers a 512-bit message digest. The first version is called whirlpool-0, whereas the second version is named Whirlpool-T and the latest version is called Whirlpool.
Purpose of Hashing:
Hashing is needed at the time of comparing a huge amount of data. You can create different hash values for different data. You can compare hashes too.
- It is easy to keep and find records of hashed data.
- You can use hashing in cryptographic applications like a digital signature.
- Hashing can create random strings that help in avoiding data duplication.
- Geometric hashing is used in computer graphics and helps to find proximity issues in planes.
What is Encryption?
Encryption is the process of securing sensitive data like usernames, passwords, credit cards, and banking details from the reach of hackers.
A piece of unencrypted information is referred to as plain text while encrypted data is known as ciphertext. Plain text can easily be read by hackers that can be used by them for malicious purposes. The ciphertext is a scrambled text that cannot be understood by the invaders if they somehow succeed in intercepting this data. The scrambled information can solely be read by the user who has access to the security key or password to decrypt this data.
Types of Encryption
Encryption is divided into Two Categories which are explained below.
1) Modern Encryption Algorithms
2) Historical encryption algorithms
1) Modern Encryption Algorithms
In this type of encryption technique, only one key is used by both the web server and the user to encrypt/decrypt the data. This key can be a number, a character string, or a word. Both the user and the webserver should have an identical key to complete the encryption/decryption process.
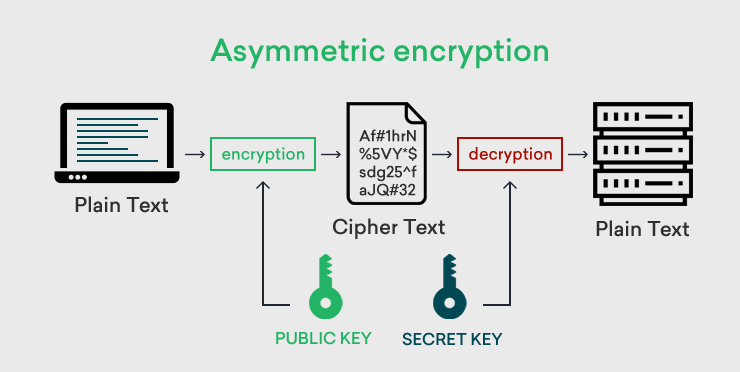
In asymmetric encryption, a pair of keys is used. One is called a public key that is shared among the customer and the website. The second key is the private key that is kept hidden by the administrator of the website. The public key is used to scramble the information coming from the user/browser and the private key is helpful in decoding this data. In this way, the info shared between the browser and the site remains safe and secure.
(C) Hybrid Encryption
As the name indicates, this is an encryption technique that takes advantage of the effectiveness of both asymmetric and symmetric encryption to minimize their shortcomings.
2) Historical encryption algorithms
Let’s understand now historical encryption algorithm details.
Shift Ciphers: The Shift Ciphers is a substitution cipher in which a shift of 3 letters against alphabetical order. For example, ‘a’ is encrypted as ‘D’ and ‘b’ is encrypted as ‘E’. However, this type of cipher is easy to break in modern times. The encrypted text will look like as below:
Source: https://crypto.interactive-maths.com/caesar-shift-cipher.html
Substitution Ciphers: Substitution Cipher as the name suggests replaces plain text with ciphertext with a key and in a specified way. It could be a single letter, triplets of letters, or a mixture of letters. A receiver decrypts the message with the opposite substitution process to get the real message.
Transposition Ciphers: Transposition Ciphers convert plain text into a regular pattern of ciphertext. In this type of cipher, alphabets in plain text are reassembled to create ciphertext. A simple type is a columnar transposition cipher where each character in plain text is written horizontally, and the ciphertext is written vertically. For example, if you write hello world horizontally, it will look like the below and its output ciphertext will look as holed LR.
Polyalphabetic Ciphers: Polyalphabetic cipher works on a substitution method where multiple alphabets are substituted with each other. Vigenere cipher is a popular method used in Polyalphabetic Ciphers. Polyalphabetic cipher uses an alphabet letter instead of a numeric key A is used for key 0 while B is used for key 1 and so on.
Nomenclator Ciphers: Nomenclator is a type of substitution cipher in which specific symbols are used to convert plain text into ciphertext. This cipher uses a sheet of letters, syllables, word substitution table, and symbols that are converted into numbers. Nomenclator was used in the 15th century for political correspondence and spying.
Learn more about What is a Cipher? Types of Ciphers in Cryptography
How Does Encryption Work?
Encryption uses a specific algorithm to encode or decode the data. Encryption algorithms are also known as ciphers and are divided into two categories, symmetric and asymmetric:
Symmetric Cipher
Symmetric Cipher uses only one key for both the encryption and decryption of data. The user uses the key to encode the information and forwards it to the web server and decodes the data utilizing the exact same key. So, without access to the key, no one can decipher this information even if they know the inner workings of encryption algorithms. Advanced Encryption Standard and Twofish are the most popular symmetric ciphers.
Asymmetric Cipher
In asymmetric ciphers, a pair of keys is utilized to scramble and unscramble the information. A public key is shared between the user and the webserver to create a session key while the private key is kept secret by the webserver. The encoded information coming from the user is decoded by the web server using the private key. This makes the asymmetric cipher safer than the symmetric cipher. The most common asymmetric ciphers include Pretty Good Privacy (PGP) and RSA (Rivest-Shamir-Adleman).
Purpose of Encryption
The primary object of encryption is to safeguard the information from spying activities. Plain text information seems a soft target for cyber thieves as they can easily read the passing plain text data between the client and the browser. When you have encrypted the website, it means all the information will be passed between two ends and remains encoded and there is no worry of prying eyes.
Encryption brings some elements with it like confidentiality, strong authentication, limited access control, and data encryption. Encrypted messages are impossible to intercept by another person. It can be only deciphered who has a private key. In case of a breach, a culprit can be traced easily, and a breach can be sorted easily. The certificate authority also authenticates the details submitted to get an SSL certificate.
Few Encryption Algorithms:
1. Advanced Encryption Standard
AES is a type of symmetric cipher that encodes 128 bits of data at a time. The key that is used to decrypt the data can be of different sizes like 128-bit, 192-bit, or 256-bit encryption. The 128-bit key ciphers the information in 10 rounds, the 192-bit key in 12 steps, and the 256-bit key in 14 stages. AES has proven itself to be highly efficient and reliable over the last few years. This method of encryption is widely used by many organizations for both the stored data and the information being transferred between two communicating sides.
2. Rivest-Shamir-Adleman
RSA being an asymmetric cipher algorithm works on two keys for encryption and decryption of the information that travels between a user and a web server. RSA algorithm works by factorizing the multiple of two large prime numbers. RSA is a weak algorithm because of the different vulnerabilities that have been exploited by hackers many times. This algorithm works slower when a large amount of information requires to be encrypted/decrypted.
3. Triple Data Encryption Standard
Triple DES is the substitute for the DES symmetric encryption algorithm. It has improved the DES cipher algorithm and uses 56-bit key data to encrypt the blocks. It applies the DES encryption process three times on every information set.
Difference Between Hashing and Encryption
Here is a summary of hashing vs encryption:
- Encryption is a two-way process where information is encoded and decoded with the help of matching key(s). Hashing is a one-way encryption technique which means that it is impossible to reverse engineer the hash value to get the plain text back.
- In encryption, the ensuing encrypted string is of variable length while in hashing, the hash value is of fixed length.
- The objective of encryption is to secure the confidentiality of the data and the purpose of hashing is to protect the integrity of the information.
- The original information shared between two communicating parties can be accessed by using the right decoding key while hashing algorithms are made efficient in such a way that the hash value remains irreversible.
Both encryption and hashing algorithms are used to protect the data from cyber-criminals. But both these schemes work differently in any given scenario. Hashing secures the data from almost all types of attacks, but it is difficult to achieve. So, for this reason, encryption has a more practical use over hashing in most cases. However, their functionality varies with the change in the given situation. Hence, you must select between the two strategies depending on the situation.
Want to Encrypt your website?
If you want to encrypt the website, it is not too late. You need to first search for the best SSL certificate provider that can provide you an authenticated SSL certificate. Then, sign up with the provider and choose the best SSL certificate for your website. As per guidance by the SSL provider, you need to complete the configuration process. After verification of the required details by a certificate authority, you will have the SSL certificate that you need to install on the server. Once you install the certificate, your website running on that server will have strong encryption.
Related Post: