Here’s an easy-to-follow guide about TLS versions. Let’s delve into the basics and understand how TLS versions work.
Securing the data is crucial for any business due to increasing digitization and online user interactions. The total data on the internet is set to reach 181 Zettabytes by 2025.
This means more information will need processing, storing, and analyzing. Security of high-volume data requires key measures like proper authentication methods, encryptions, and access control.
SSL/TLS certificates enable data encryption using cryptographic algorithms that you can leverage to secure sensitive information. These digital certificates enforce HTTPS protocols to secure the data exchanges between a server and a browser. However, such certificates use TLS protocols, which have multiple versions.
So, you need to understand which TLS version is used for your digital certificate and how secure it is for your systems. This article will enable you to understand different TLS versions, their difference from an SSL protocol, and how to check if you have the correct version.
What is TLS?
Transport Layer Security (TLS) ensures data privacy and integrity across all communications on the internet. It is a security protocol, an upgraded version of SSL communications. TLS secures the data exchanged between the browser and server.
How Does TLS Work?
TLS protocol consists of record and control protocols. The record protocol offers a standard packaging for TLS messages.
On the other hand, the control protocol has three elements:
- Handshake protocol
- Change cipher spec protocol
- Alert Protocol
When a user initiates the session by sending a TLS message on port 443, all the data users need is fragmented according to different protocols like handshake protocol, change cipher spec protocol, and alert protocol.
Further, the fragmented data is compressed, and a MAC (0,16 or 20 bytes) is appended to this information. The data packet is encrypted using a symmetric encryption algorithm, and a security key is sent.
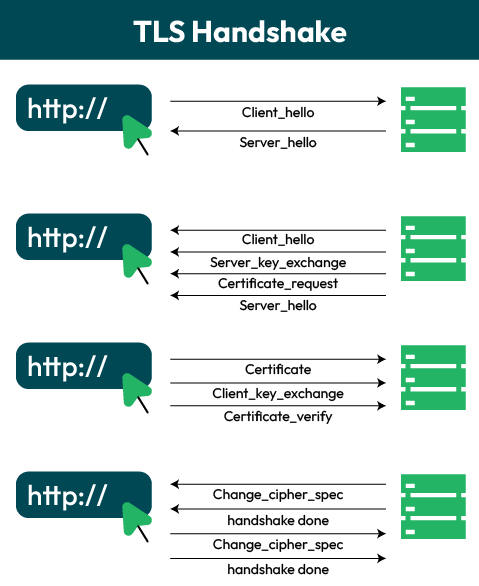
The TLS record protocol header is added to the data file and passed to TCP. The following process in TLS session establishment is a handshake protocol. Here are three critical steps of the TLS handshake process.
- Establish security capabilities
- Server authentication and key exchange
- Client authentication and key exchange
First, the client or browser establishes different security capabilities for the handshake. This includes defining the protocol version, session ID, cipher suite, compression approach, and initial random numbers.
In the next phase, the server will send an SSL certificate key exchange and request a certificate from the browser to verify identity. The last step will have the change cipher suite complete the handshake protocol.
Once the handshake is complete, your system can secure end-to-end data exchange sessions. Now that you know how TLS works, it’s time to understand its benefits.
Benefits of TLS
SSL/TLS certificates enforce the TLS protocols and ensure security for data on your servers. However, there are many other benefits of using TLS protocols beyond data protection.
- At a superficial level, TLS protocols ensure secure data exchange between your web servers and browser.
- It allows you to maintain data integrity, which is crucial if you are an enterprise dealing with multiple information sources.
- Due to TLS security, customers will trust your business more for transaction improving conversions.
- Complying with crucial data regulations and protection guidelines is easy with TLS protocols like GDPR, HIPAA, and PCI DSS.
- TLS certificates have pre-built security features like HMAC (Key-Mashing Authentication Code), which uses robust MAC authentication before the handshake process.
- TLS protocols offer more granular control for secure and vulnerable data during the exchange.
List of TLS Versions
The first version of TLS was introduced in 1999 for communications privacy over the internet. Since then, there have been many versions over the years. For example, two TLS versions were deprecated in 2021(TLS 1.0 and 1.1).
Businesses need to check which TLS version they use for web apps to understand the impact on data security. For example, if you are using version 1.0 or 1.1, which are deprecated, your web app may face compatibility issues with several browsers.
At the same time, TLS 1.2 is far more secure but has lower latency. The 1.3 version makes more sense, so understanding these TLS versions’ differences is crucial.
Let’s know each of the versions.
#1. TLS 1.0
TLS 1.0 is one of the oldest versions introduced as an upgrade to SSL 3.0 for the Netscape/Microsoft browser. There are many similarities between TLS version 1.0 and SSL 3.0, and it was not a considerable upgrade. However, small changes that TLS 1.0 had pre-built provided better interoperability with the SSL 3.0 version.
This is why many businesses even downgraded their sites to SSL 3.0. According to a report, 33% of websites support downgrade to SSL3.0. Usage of the TLS 1.0 version is limited now due to deprecation back in 2021.
#2. TLS 1.1
TLS 2.0 was released in 2006 to update TLS 1.0 with some key differences and upgrades, like
- More protection from cipher-block chaining attacks
- The initialization factor (IV) was changed from implicit to explicit
- Critical changes on how to handle padding errors
- Support for parameters needed to register on Internet Assigned Numbers Authority (IANA)
It uses deprecated algorithms like MD5 and SHA-1 to secure your data, which is why both TLS 1.0 and 1.1 were deprecated.
#3. TLS 1.2
TLS 1.2 is one of the most popular protocols used by several businesses. According to a report, 95.8% of websites still use TLS 1.2 despite the release of the 1.3 version. This TLS version enables your server to select ciphers supported by browsers and websites. It also supports extra data modes for authentication and encryption.
TLS 1.2 is crucial for businesses working with government authorities on different projects because it supports advanced cipher suites. The National Institute of Standards and Technology(NIST) has specific guidelines for implementing TLS, and this version supports it through an advanced cipher suite.
TLS 1.2 is also far more secure than earlier versions due to two rounds of handshake phases. It requires two handshake protocol executions to communicate, making the data exchange secure.
#4. TLS 1.3
TLS 1.3 is the latest protocol that you can use to enforce HTTPS and encrypt data securely. A significant improvement that TLS versions did not provide earlier was rapid handshakes, and that is where TLS 1.3 has been phenomenal. It requires only one round trip or single handshake execution compared to two round trips in TLS 1.2.
Further, if a website has already connected with the server, the handshake does not require a round trip on reconnection. This reduces the connection latency, making the user experience seamless and secure.
Now that you know what different TLS versions and the significant security features they offer, it’s time to address another dilemma- “is TLS different from SSL?”
TLS vs. SSL: Two Sides of a Coin!
TLS is an upgrade to SSL protocol, which helps secure communication between two devices or applications in a network. Secure Sockets Layer (SSL) is an older protocol used to establish trust among users and authenticate the identity of web app publishers. TLS versions are successors to SSL versions and are used to enforce HTTPS protocol.
SSL and TLS use digital certificates to secure data but operate distinctly from each other. For example, the SSL handshake process is explicit. On the contrary, TLS versions use implicit handshake.
Here are some critical differences between SSL and TLS versions.
Authentication process
SSL and TLS both use MACs for authentication and maintaining the integrity of the messages. The record protocol uses a secret key to generate the MAC code assigned to the message. However, the algorithm these protocols use for MAC generation differs for SSL and TSL.
SSL protocols use the MD5 algorithm to generate MAC, which is outdated. However, TLS uses an HMAC algorithm, which is far more complex and secure.
Upgraded cipher suite
SSL uses an older cipher suite with several algorithms for key generation and data encryptions. TLS has an upgraded cipher suite, which offers more security than the SSL version. Comparing the SSL and TLS, cipher suite efficiency comes into play, where the latter has the edge over the former protocol.
Types of alerts
SSL alerts about errors through two major types- “warning” and “fatal.” However, despite the alert message connection can continue. For the fatal alert, the connection needs to be terminated. At the same time, TLS offers an option to close the connection after the warning.
The difference between SSL and TLS is crucial to ensure the security of your systems. But you also need to check whether your web app is using TLS/SSL protocol is important.
How to check the TLS Version?
Knowing the TLS version is crucial to understanding what level of security your website has, but the process of checking it differs based on the browser and operating system.
Steps to check TLS Version on Linux
NMAP and OpenSSL can be used if you want to find TLS versions for Linux servers. NMAP is a network scanning tool that you can use to get information on remote systems, including which version is active.
You need to install nmap and use the command,
nmap --script ssl-enum-ciphers -p 443
It initiates a scan and displays data about TLS cipher suites supported by the server. Further, it provides detailed information on supported protocols.
Another way to check TLS is by using the OpenSSL client tool. You can install OpenSSL from the official website and use the following command to check the TLS version:
#openssl s_client -connect
You can also use browsers to check TLS versions besides OpenSSL and NMAP.
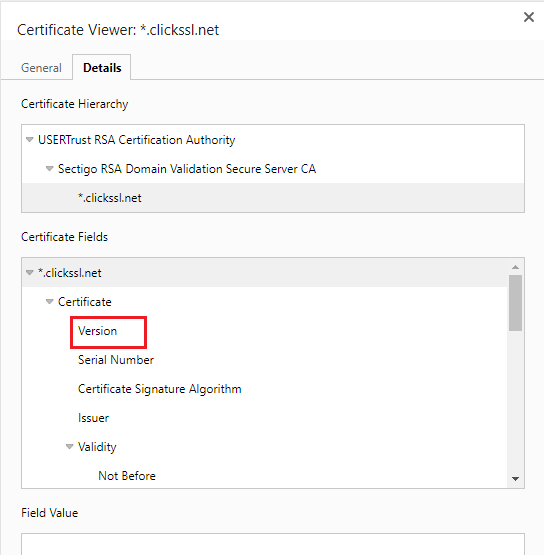
Steps to check TLS Version on Google Chrome
Here are the steps to check the TLS version on Chrome for your website,
Step 1: Enter the URL to check the TLS version in Chrome’s address bar.
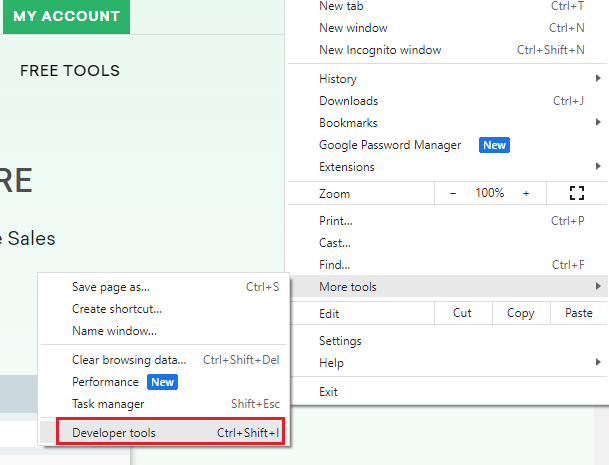
Step 2: Go to the three dots on top of the right-hand side of your browser and click on more tools.
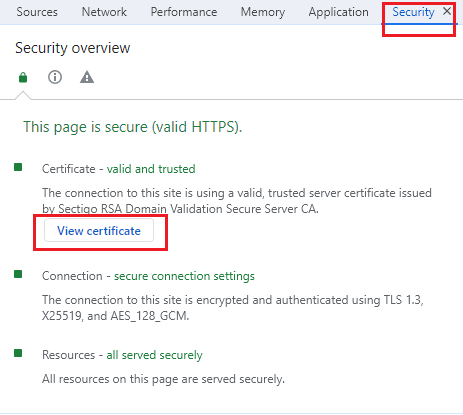
Step 3: Now select “Developer Tools” and then “Security”
Step 4: Click on the “View Certificate” and you can check the version on detail tab.
Conclusion of TLS Versions
Knowing which TLS version you are using helps in understanding the security your system have against cyberattacks. It also allows you to determine which type of handshake process it follows, MAC generation method it uses, and support across browsers. Using a deprecated version can harm your system, and customers can loose trust in your brand.
With the steps discussed on how to check TLS versions you can find the version used for your website. If you are using the right version like TLS 3.0 or 2.0, it will secure data but using deprecated versions can lead to cyberattacks.
Related Post: