Asymmetric Encryption (public key cryptography) is type of encryption which use to encrypt and decrypt data. Learn more about what is Asymmetric Encryption.
Ever since the market transition from physical to digital is increasing, the security issue is becoming graver than ever. Digitalization has completely enhanced the data collection technique by making it easy to preserve, access and share. Computers and hard disks have become the storage of data and eliminated the need for files and folders.
But this data is at risk of being invaded by hackers and cyber-criminals, either from their storage locations or during the transfer process.
The best way to secure in-transit data is to encrypt the same by installing an SSL certificate.
There are two types of encryption.
- Symmetric Encryption
- Asymmetric Encryption
This article will discuss asymmetric encryption, its characteristics, it’s functioning, and its pros and cons.
But first, let’s begin with what is encryption.
What Is Encryption?
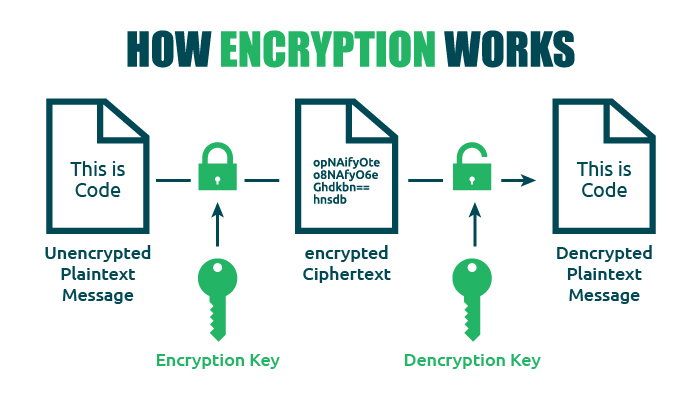
Encryption is a data protection process, which encodes the information using cryptographic keys and encryption algorithms and creates a non-readable text (ciphertext).
The beauty of encryption security is that only the authorized recipient can decode and access the message since it requires a secret key for the same, which is with the recipient only.
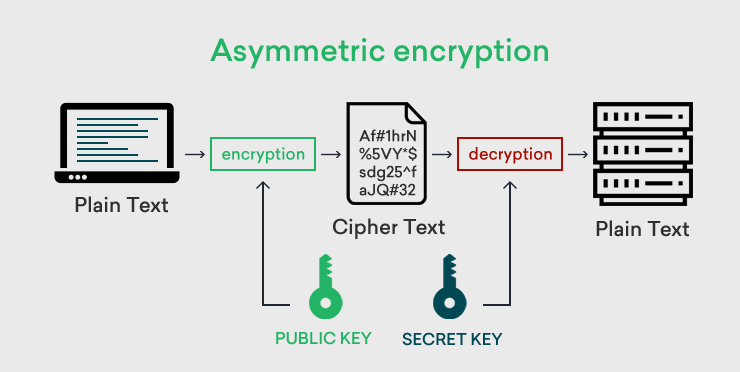
The above image clearly states how the encryption key encrypts the data into an encrypted ciphertext and how the decryption key deciphers the message into plain text again.
There are two types of encryptions, and hence the keys used in the process are either symmetric or asymmetric depending on the type of encryption used.
The digital security key is a string of characters.
An Overview of the Two Types of Encryptions:
As stated above, encryption can be done in two ways.
#1. Symmetric Encryption:
Symmetric encryption uses only one key to complete the full encryption and decryption process. i.e., the key that encrypts the data is used for decrypting the same too.
#2. Asymmetric Encryption:
Asymmetric encryption uses two different keys to complete the entire process. i.e., the data is encrypted using the encryption key, and the same is decrypted using the decryption key.
We already shared the difference between Symmetric vs Asymmetric Encryption but this article is about asymmetric encryption, so let’s discuss the same in detail.
What Is Asymmetric Encryption? A Definition and Explanation
As stated above, Asymmetric Encryption, or Public-key Cryptography, as you name it, uses a pair of keys for encrypting and decrypting messages. This key pair is mathematically related to each other with algorithms and is called the Public Key and the Private Key.
The Public Key, as the name defines is publicly available for all senders of the message who wish to secure their message with encryption. In contrast, the Private/Secret Key is secured and only accessible to the authorized recipient of the message, who can read the message by decrypting the same.
History of Asymmetric Encryption:
Whitfield Diffie and Martin Hellman (researchers at Stanford University) were the first persons to suggest asymmetric encryption in 1977 publicly.
This concept was also suggested a few years before these researchers by James Ellis, who worked for the BI (British Intelligence) and GCHQ (Government Communications Headquarters). However, this information remained classified till 1977.
Later these algorithms were independently developed by individual cryptographers and hence were named the same after their discoveries.
| Type of Algorithm | Discovered By | Year of Discovery |
|---|---|---|
| D-H Key Exchange Protocol | Whitfield Diffie & Martin Hellman | 1976 |
| The RSA Algorithm | Clifford Cocks | 1973 |
Ron Rivest, Adi Shamir, and Leonard Hellman reinvented the RSA algorithm in 1977, which was published (Communications of the ACM) in 1978.
Hence, the RSA algorithm signifies its inventors and is named after them.
In the current scenario, RSA is defined as the basic asymmetric encryption algorithm. This algorithm is used in a majority of the digital securities like SSL/TLS certificates, digital signatures, SSH (Secure Shell), etc.
What Does Asymmetric Encryption Do?
Asymmetric encryption uses two separate keys that are linked to each other with a mathematical algorithm for performing the encryption and decryption process. The same is opposite to symmetric encryption, wherein only a single key is used for the entire process.
Asymmetric encryption has another name, i.e., Public Key Cryptography/Encryption because the encryption key can be accessed publicly by all who wish to encrypt the message. This is a very crucial internet security solution because of the private key being non-shareable. This makes asymmetric encryption loved by web owners all over the globe.
This method is usually used to:
- Validate the website
- Confirm the data integrity
- Exchange the keys
Symmetric encryption is the best security for bulk data encryption, but asymmetric encryption is ideal for small data like websites or other minor data. The same is possible by installing an SSL/TLS certificate on the website.
The asymmetric encryption process commences with generating two keys, which are later verified by the browser and server, and a single session key is created. Then, this encryption process begins using symmetric encryption by using the session key.
Characteristics/Uses of Asymmetric Encryption:
#1. Securing Data and Exchanging Keys in Public Channels:
The main motto of asymmetric encryption is to encrypt data on public platforms by ensuring authenticity and data integrity. But, since two different keys are used in the asymmetric encryption process, no exchange of keys is required.
#2. Large Asymmetric Encryption Keys:
This encryption is quite secured, thanks to its large, distinct, and arbitrary created numeral strings. Websites all around the world use SSL certificates for securing their website data.
Hence, it’s obvious that each website has a unique set of keys for the encryption and decryption process. Just imagine the randomness in strings used in the key generation process, making these keys unique and unpredictable.
#3. Strong Encryption Algorithms:
This encryption uses all the popular and secured key exchange algorithms like Diffie-Hellman, ElGamal, RSA, DSA, and ECC. The lengthy keys (1024-bit or 2048-bit), etc., which are used in this process, strengthen the communications between the client and server.
Example: If a key has 2048-bit encryption security, it means that there are approximately 2048 combinations.
Guessing is a tough call when lengthy keys are used in the process, and even if the help of a supercomputer is taken, it takes hundreds of years to guess the same.
This makes asymmetric encryption more favorable as compared to the other web securities.
#4. Retains Confidentiality:
Non-Sharing of the two keys eliminates the need to distribute the same, and hence confidentiality is maintained in the process.
Example: Sender uses encryption key and receiver uses decryption key, so confidentiality is assured.
#5. Retaining Authenticity of Digital Signatures:
The sender attaches digital signatures to confidential messages. The same is encrypted with a private key. When the receiver gets the message, he can use the public key to validate the sender’s legitimacy.
#6. Security of Information:
Data integrity and data security are ensured in asymmetric encryption.
#7. Non-repudiation by Initiator:
The sender can’t reject the information sent by him, i.e., the message’s originator cannot repudiate the same after sharing it with others. This keeps asymmetric encryption ahead of symmetric encryption.
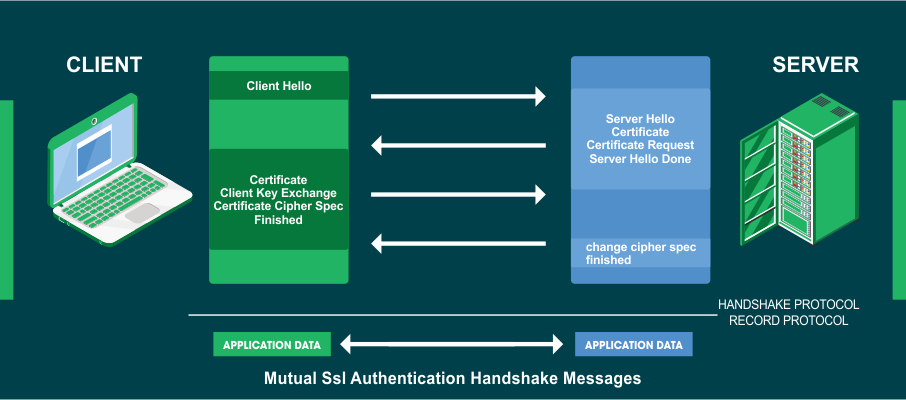
How Asymmetric Encryption is used in SSL/TLS Certificates:
Let me tell you that SSL/TLS certificates use dual encryption methods for securing website information. Though asymmetric encryption is more favorable, its main drawback is the processing time. In addition, lengthy keys slow down the same, which favors symmetric encryption making it essential for the success and completion of the process.
The key authentication via asymmetric encryption is done by both parties, i.e., the browser and the server. First, they generate a common key (session key) and commence the process via symmetric encryption. This saves a lot of time without compromising on data confidentiality and website security.
This is named the SSL/TLS Handshake Process.
How Does Asymmetric Encryption Work? Let’s Explore This Concept with An Example
Before moving forward to the asymmetric encryption example, let me take an imaginary example that may help you understand this complex process in a simple way.
Suppose you send a treasury box to someone via courier. It would help if you secured it before sending the same. For example, you have a pair of keys, of which one is sent to the box’s receiver. You can secure it with a lock using your key and send the same. The recipient will receive the locked treasure box and open the same with his key and get his valuables.
The above process is used in securing digital information too. The data transfer on the internet always happens in plain text. When the sender has to send a message, he will encrypt the same with an encryption key, and the text will get converted into ciphertext. The recipient of the message owns the decryption key with which they can decipher the ciphertext into plain text and read the same.
Note: The decryption key is a secret key and lies only with the recipient.
The Advantages & Disadvantages of Asymmetric Encryption:
Each digital security has its advantages and disadvantages, and the same stands true for asymmetric encryption also.
Advantages Asymmetric Encryption:
#1. More Secure than Symmetric Encryption:
This process involves two keys which make this encryption more reliable than symmetric encryption. First, this encryption uses lengthy keys like 1028-bit, 2048-bit, 4096-bit, etc., compared to its symmetric counterpart, which uses small key lengths like 128-bit, 256-bit, etc., which makes this encryption more secured.
#2. More Secure in case of More End Users:
Single key sharing in symmetric encryption is risky when more end users are involved. The success and key secrecy are interrelated, i.e., the process is bound to succeed due to the confidentiality of the key. The chances of the key being compromised are very low, which is adverse in symmetric encryption, wherein the key is shared amongst many users.
#3. Easy Key Distribution:
Two different keys make the distribution task easy. The public key can be used by many users who want to encrypt their information.
But in symmetric encryption, the key distribution process needs to be done with caution because if the key is compromised, it may affect many servers and networks, thus causing damages.
#4. Feasible for Digital Signatures:
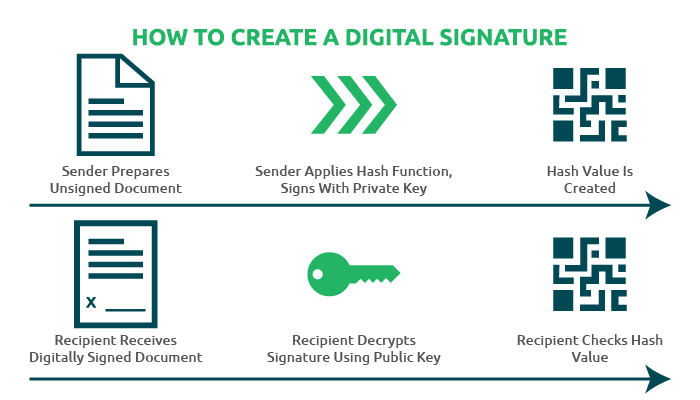
Digital signatures are used to authenticate electronic documents and applications apart from identity verification. They use cryptographic hashes, which allow the recipient to check the legitimacy of the document and judge whether the same is modified or not.
These signatures use an asymmetric encryption method wherein the sender signs the electronic document with a private key via cryptographic hashes. The recipient decrypts the signature using the public key for verifying the hash and the document.
Disadvantages Asymmetric Encryption:
#1. Slow Processing Speed:
The use of two keys and the length of keys make this entire process time-consuming and complex.
#2. Key Management:
The public infrastructure of asymmetric encryption requires web owners to implement PKI (public key infrastructure) to handle SSL certificates. A PKI consists of managing the issuance of SSL and re-issuance in case of expiry of SSL certificates via trusted CA’s (Certificate Authorities).
#3. Bulky Process for Large Data:
The asymmetric keys are a huge load on the servers due to their length and complexities. Hence, when small data needs to be encrypted, this process is ideal, but as stated before, securing large chunks of data is best done with symmetric encryption.
#4. Loss of Private Key makes Decryption Impossible:
If the recipient loses the private key, the decryption process becomes impossible, and the recipient will not be able to read the message.
If the private key falls in the hands of an intruder, he can decrypt and read all the messages.
Wrapping Up:
No security is 100% perfect, and neither are the asymmetric encryption algorithms, but still, they offer incredible protection and help create secured tunnels for data communication between third parties.
When SSL certificate security is involved, they use a mixed approach by using these types of encryptions to secure browser-server communications.
I hope the above explanation gives you a clear view of asymmetric encryption, it’s functioning, characteristics, and pros and cons.
There is no doubt that asymmetric encryption paves a secured platform for exchanging confidential information, which helps propel the e-commerce industry to greater heights.