Several internet users and online businesses often fail to realize that symmetric encryption is part of everything they do online. In other words, symmetric encryption allows internet users to make online banking transactions securely and order products and services online.
However, what is symmetric encryption, and why is it essential for businesses and others? If you want to ensure greater security of your business, you need to understand how symmetric encryption works clearly.
In this article, we will be talking about everything that you need to know about symmetric encryption.
What Is Symmetric Encryption?
Symmetric encryption, also called symmetric-key cryptography, can be described as a process or technique where a secret key is used for decryption and encryption functions. Data will be converted to a format during symmetric encryption to prevent unauthorized users from inspecting or reading it.
The method of symmetric encryption is the exact opposite of asymmetric encryption, which uses two separate keys. One key (public key) is used for encryption, and another (private key) is used for decryption in asymmetric encryption.
In other words, symmetric encryption can be defined as a type of encryption, which uses the same key to decrypt and encrypt data. Here is a quick overview of how the process of encryption generally works.
How Does Symmetric Encryption Work?
In the first step of the encryption process, an encryption key is used by the sender for encrypting their message. The encryption key usually consists of a string of numbers and letters in most cases.
In the second stage of the process, the encrypted message, called a ciphertext, will look like a bunch of scrambled letters, which means that no one will be able to access or read them. Finally, the message recipient will use a decryption key for transforming the encrypted message into its original form.
Only the recipient and sender will access and read the data once it has been encrypted. This is one of the major reasons why symmetric encryption is also called symmetric key encryption, symmetric cryptography, secret key cryptography, and secret key encryption.
Having just a single key for both decryption and encryption functions will simplify the process of encryption. This is because you are applying just one key to transform the plaintext into an unreadable ciphertext.
One of the major advantages you can enjoy by choosing symmetric encryption is that it ensures data confidentiality and privacy without using multiple keys. Therefore, symmetric key encryption is beneficial when it comes to encrypting files and databases.
Examples of Symmetric Encryption
As mentioned earlier, the process of symmetric encryption is beneficial in several cases. For instance, symmetric encryption will enable you to encrypt financial or banking-related data along with helping you with data storage. Here are a few common examples of symmetric encryption.
What is Symmetric Encryption Used For?
Banking
Most of you would have probably heard about PCI DSS. The PCI DSS or Payment Card Industry Data Security Standard can be defined as a set of twelve requirements that businesses accepting credit card payments will have to adhere to.
Do you know that one of the integral components of PCI DSS compliance is symmetric encryption? It comes under the third requirement that primarily focuses on offering adequate protection to the data of cardholders or customers.
Data At Rest
Data at rest refers to the current state of your business data when it is sitting on a device or server. In other words, data at rest means that the data will not be in transit, which implies that the data is not being sent across the internet or a network.
Most businesses will have large volumes of confidential and important business data, which they don’t want unauthorized people to access or read. If you want to prevent unauthorized individuals from gaining access to such data, you must use the at-rest data encryption method.
It is important to note that the method of symmetric cryptography is also used to verify that the sender of an email or message is precisely who they claim to be. Finally, symmetric cryptography is also used for the generation of random numbers.
The Role Of Symmetric Key Encryption In Website Security
Symmetric encryption is a crucial part of the PKI ( Public Key Infrastructure) ecosystem. This, in turn, allows secure communication across the internet by transforming readable data into unrecognizable text.
Most of you would have probably noticed a padlock in the URL bar of your internet browser when visiting websites. The appearance of a grey padlock indicates that an SSL or TLS certificate has been installed on the website, which means that you are using an encrypted and safe connection to send and receive data.
This also indicates that your internet browser has gone through the below-mentioned processes.
- Authenticating the server of the website
- Negotiating with the website server on which encryption algorithms has to be used
- Symmetric session keys generation
HTTPS works by making use of an asymmetric encryption method for initially authenticating the server of a website. The same type of encryption is also used to exchange the symmetric session keys, which is a crucial part of a TLS handshake process.
After the processes mentioned above are completed, symmetric encryption is used for the data encryption process, which will take place during a website browsing session. The TLS handshake does the following things.
- Allows the webserver to authenticate with the web browser of the customer or client
- Establishes parameters that should be used to secure communication, such as deciding which encryption algorithm to use
- Determines the key exchange protocol that should be used
- Creates a session key
The major reason for the change to the symmetric encryption method is that it is less resource-intensive and faster when compared to asymmetric encryption. This is especially true when you encrypt large volumes of data, which means that symmetric encryption is the best option for large companies and banks that need to encrypt large amounts of data.
The Key Should Remain Secret For Symmetric Algorithm To Work
You would have probably guessed by now that the key should remain secret for the process of symmetric encryption to work. This means that only you and the recipient should know the key.
However, if that’s not the case, and if someone else knows it, they will decrypt the data and access it easily.
When that happens, the encryption process will remain pointless, so it is important to keep the key secret. It is best not to store private or secret keys in internet-facing environments to prevent unauthorized individuals from accessing the data.
The best thing you can do is hide private or secret keys, where no one will be able to steal, access, or find them. In other words, you will need to do everything to ensure that the keys will not end up in the hands of unauthorized individuals.
How to Share a Key Securely to Facilitate Symmetric Encryption
Let us assume that you need to share some urgent but secret message to someone living in a different country, but they do not have access to a key for decrypting the messages. If that’s the case, you will need to get a shared key for the receiver so that they can decrypt it.
This implies that you will need to share the secret key through the internet, which is not secure. This is because your internet connection will be getting bounced through several touchpoints during its journey.
The issue with this is that your government, cybercriminals, or someone else might intercept the key and decrypt the message without any hassles. This is commonly known as MitM or man-in-the-middle attack. This means that sharing keys across the web is not a good idea. Due to this, we will need to implement alternative methods such as Diffie-Hellman or RSA.
Symmetric Encryption Algorithms
Symmetric algorithms can be divided into two separate categories, and they are called block and stream ciphers. Block ciphers serve to encrypt data in blocks or chunks, while stream ciphers encrypt data one at a time. Here are some of the most common types of Symmetric-key algorithms.
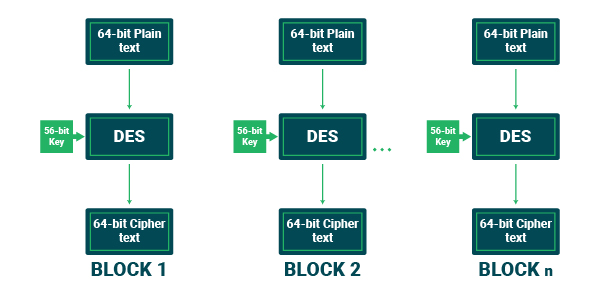
#1. DES (Data Encryption Standard)
Data encryption standard is a form of block cipher, which encrypts data in 64-bit chunks or blocks by using just one key that comes in three different sizes ( 192-bit, 128-bit, and 64-bit keys). However, it is important to note that one bit among every 8 bits will be a parity bit.
Data encryption standard is one of the earliest symmetric encryption algorithms, but they are no longer suitable for use. This is because DES is viewed by many as an insecure method, which has become deprecated.
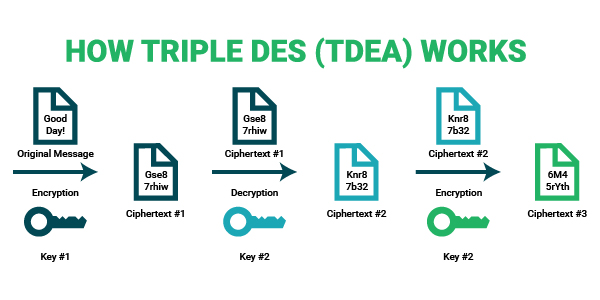
#2. TDEA/3DES ( Triple Data Encryption Standard)
What makes TDEA or 3DES different from DES is that it uses either 2 or 3 keys, which in turn enables this symmetric algorithm to perform multiple rounds of encryption. As a result, Triple Data Encryption Standard is a lot more secure when compared to DES, but it is not as secure as the Advanced Encryption Standard.
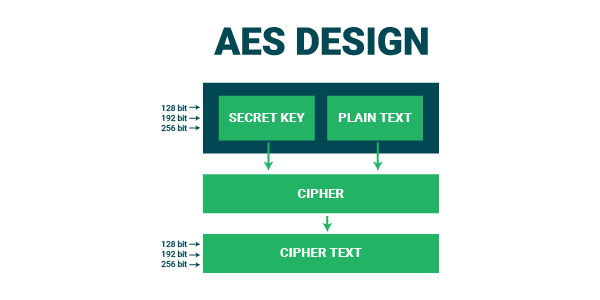
#3. AES ( Advanced Encryption Standard)
AES or Advanced Encryption Standard is a type of symmetric algorithm that you are more likely to find across the web. It is a lot more efficient and secure when compared to both the Triple Data Encryption Standard and Data Encryption Standard.
However, it is important to note that AES works differently compared to both the methods mentioned above. This is because AES is not based on the Feistel Cipher; instead, it is based on a substitution permutation network.
Conclusion
As mentioned earlier, symmetric encryption is a very old encryption method, but it is still widely used due to the higher security and safety it guarantees. If you want to ensure that data sent across the web is safe and can’t be accessed by unauthorized users, then symmetric encryption will help you do that with ease.
Recommended Reading: